cybersecurity
See the following -
Is There Ebola On That Smartphone?
Medical staff treating patients with Ebola and other communicable diseases in Africa face a novel kind of smartphone security problem...
- Login to post comments
IT Spending Up 2.1 Percent In President's Budget
The Obama administration budget for fiscal year 2014 includes a modest increase in overall IT spending. Total outlays are just under $82 billion, with $42.3 billion in civilian-agency IT spending, and $39.5 going to defense IT. Read More »
- Login to post comments
Jonathan Perlin’s ‘Elevator Pitch to the President’ on Health IT
 What would you say if you had to make an “elevator pitch” in just three to five minutes to the President of the United States about what to focus on in terms of the nation’s healthcare system? That was the question put to panelists at a Sept. 26 meeting of the National Academy of Medicine (NAM). Jonathan Perlin, M.D., chief medical officer of Hospital Corporation of America (HCA), responded: “It’s all about the data”...
What would you say if you had to make an “elevator pitch” in just three to five minutes to the President of the United States about what to focus on in terms of the nation’s healthcare system? That was the question put to panelists at a Sept. 26 meeting of the National Academy of Medicine (NAM). Jonathan Perlin, M.D., chief medical officer of Hospital Corporation of America (HCA), responded: “It’s all about the data”...
- Login to post comments
Lessons Cyberdefense May Be Able To Teach Us About Managing Ebola
David Gewirtz presents lessons taken from the world of cybersecurity and cyberwarfare that may be food for thought for those attempting to prevent the Ebola outbreak from spreading in the United States...
- Login to post comments
Linux ETC
 Linux ETC is a Linux training and Open Source consulting firm. We are the one-stop for stable, secure, and cost-effective information technology solutions. At The Linux ETC Company, we strive for a common balance between our trainers and our consultants. Our trainers consult, and our consultants train. By using this balanced business philosophy, our consultants are continuing to learn and educate themselves to keep in the cutting edge with today’s fast-changing computer world. This is enhanced by real-time practical experience of putting their knowledge and skills to use for our clients, and in turn, bringing those experiences back to our training students.
Linux ETC is a Linux training and Open Source consulting firm. We are the one-stop for stable, secure, and cost-effective information technology solutions. At The Linux ETC Company, we strive for a common balance between our trainers and our consultants. Our trainers consult, and our consultants train. By using this balanced business philosophy, our consultants are continuing to learn and educate themselves to keep in the cutting edge with today’s fast-changing computer world. This is enhanced by real-time practical experience of putting their knowledge and skills to use for our clients, and in turn, bringing those experiences back to our training students.
- Login to post comments
Linux Whips Apple's macOS in the Race to the Automobile CarOS
 I don't think much about it while I'm driving, but I sure do love that my car is equipped with a system that lets me use a few buttons and my voice to call my wife, mom, and children. That same system allows me to choose whether I listen to music streaming from the cloud, satellite radio, or the more traditional AM/FM radio. I also get weather updates and can direct my in-vehicle GPS to find the fastest route to my next destination. In-vehicle infotainment, or IVI as it's known in the industry, has become ubiquitous in today's newest automobiles...
I don't think much about it while I'm driving, but I sure do love that my car is equipped with a system that lets me use a few buttons and my voice to call my wife, mom, and children. That same system allows me to choose whether I listen to music streaming from the cloud, satellite radio, or the more traditional AM/FM radio. I also get weather updates and can direct my in-vehicle GPS to find the fastest route to my next destination. In-vehicle infotainment, or IVI as it's known in the industry, has become ubiquitous in today's newest automobiles...
Maintaining Health Data Privacy in Precision Medicine Push
As cybersecurity threats continue to evolve and put PHI at risk, precision medicine guidelines need to be updated to account for new health data privacy threats, according to a recent opinion piece published in the Oxford University Press. The Johns Hopkins Hospital and Health System Senior Counsel Jennifer Kulynych, JD, PhD explained that data re-identification methods are not foolproof, and it can be difficult to determine exactly how individuals’ genomes are being used...
- Login to post comments
McAfee Labs Threats Predictions Report Previews Cyber Threats for 2017 and Beyond
 Intel® Security today released its McAfee Labs 2017 Threats Predictions Report, which identifies 14 threat trends to watch in 2017, the most critical developments to watch for in cloud security and the Internet of Things (IoT) security, and the six most difficult-to-solve challenges facing the cybersecurity industry. The report reflects the informed opinions of 31 Intel Security thought leaders. It examines current trends in cybercrime and makes predictions about what the future may hold for organizations working to take advantage of new technologies to both advance their businesses and provide better security protection...
Intel® Security today released its McAfee Labs 2017 Threats Predictions Report, which identifies 14 threat trends to watch in 2017, the most critical developments to watch for in cloud security and the Internet of Things (IoT) security, and the six most difficult-to-solve challenges facing the cybersecurity industry. The report reflects the informed opinions of 31 Intel Security thought leaders. It examines current trends in cybercrime and makes predictions about what the future may hold for organizations working to take advantage of new technologies to both advance their businesses and provide better security protection...
- Login to post comments
Medical Devices Could Be Lethal in Hands of Hackers
It is embarrassingly easy to hack medical devices, experts warn, creating a new security threat that could have life-or-death consequences. Among the many devices vulnerable to hackers are drug infusion pumps, which could be jimmied to deliver a lethal dose, anesthesia machines and Pacemakers. Many medical devices are produced by legacy companies that are new to designing software...
- Login to post comments
Medical Devices Hit by Ransomware for the First Time in US Hospitals
Is it possible that North Korea used a stolen National Security Agency hacking tool to infect medical devices at U.S. hospitals? Turns out, in today's topsy-turvy world, it is. When the NSA cyber weapon-powered WannaCry ransomware spread across the world this past weekend, it infected as many as 200,000 Windows systems, including those at 48 hospital trusts in the U.K. and so-far unnamed medical facilities in the U.S. too. It wasn't just administrative PCs that were hacked, though. Medical devices themselves were affected too, Forbes has learned...
- Login to post comments
MITRE crowdsourcing analytics to bolster cybersecurity
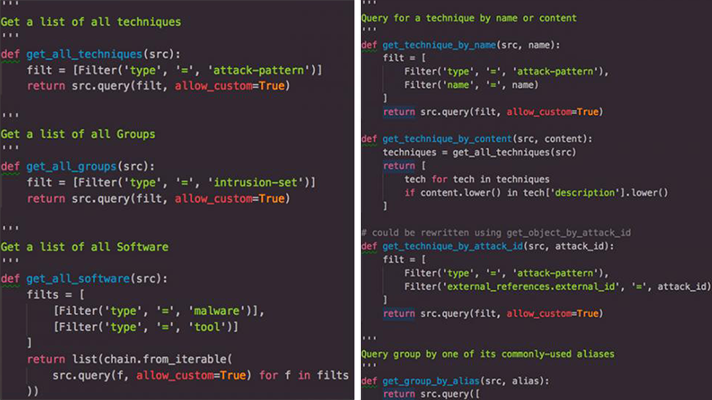 Threat detection response has historically been more reactive than proactive. Organizations often wait until suspicious activity occurs on the system to find bad actors, and intrusions are commonly difficult to detect. While perimeter security is crucial, in this era of highly-sophisticated cyberattacks, it’s no longer enough. To that extent, MITRE has been working to partner with the National Health Information Sharing and Analysis Center (NH-ISAC) to research cyberthreat tactics and share those results with hospitals and communities through its Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) analytics method.
Threat detection response has historically been more reactive than proactive. Organizations often wait until suspicious activity occurs on the system to find bad actors, and intrusions are commonly difficult to detect. While perimeter security is crucial, in this era of highly-sophisticated cyberattacks, it’s no longer enough. To that extent, MITRE has been working to partner with the National Health Information Sharing and Analysis Center (NH-ISAC) to research cyberthreat tactics and share those results with hospitals and communities through its Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) analytics method.
- Login to post comments
NASCIO Recognizes Outstanding Achievements in State IT: Finalists Announced for 2017 NASCIO State IT Recognition Awards
 The National Association of State Chief Information Officers (NASCIO) has selected 32 finalists across 11 categories for the State IT Recognition Awards. This is the 29th consecutive year NASCIO has honored outstanding information technology achievements in state government through the awards. Projects and initiatives from NASCIO member states, territories, and the District of Columbia were eligible for nomination. NASCIO members served as volunteer judges to review the 100+ submissions, narrowing the nominees down to finalists in each category. From these finalists, a recipient will be announced during an awards dinner at the upcoming NASCIO Annual Conference this October in Austin, Texas...
The National Association of State Chief Information Officers (NASCIO) has selected 32 finalists across 11 categories for the State IT Recognition Awards. This is the 29th consecutive year NASCIO has honored outstanding information technology achievements in state government through the awards. Projects and initiatives from NASCIO member states, territories, and the District of Columbia were eligible for nomination. NASCIO members served as volunteer judges to review the 100+ submissions, narrowing the nominees down to finalists in each category. From these finalists, a recipient will be announced during an awards dinner at the upcoming NASCIO Annual Conference this October in Austin, Texas...
- Login to post comments
Netflix Does Its Tech Homework
When people here and elsewhere look at Netflix (NFLX) they see a content company, a sales channel for Hollywood. They may compare it with other channels or they may focus on its growing costs. What no one seems to do is consider Netflix as a technology play. So let's look at that. Read More »
- Login to post comments
Netflix Vs. Healthcare.Gov
What could possibly have motivated the Centers for Medicare and Medicaid Services to refuse to release even a single document about the healthcare.gov site’s security in response to a Freedom of Information Act request submitted by the Associated Press? The AP announced that its request had been refused last week and, by way of explanation, cited a statement from CMS spokesman Aaron Albright that “releasing this information would potentially cause an unwarranted risk to consumers’ private information.”...
- Login to post comments
